The purpose of this article is to inform you about the risk of intrusion and eavesdropping by cutting the cable.
Please do not attempt this outside of your own environment.
Why Intrusion through LAN Cables?
I am Yasui from Cyber Defense Institute, Inc.. I have been working on improving Industrial Control System (ICS) security based on my experience in developing ICSs for many years. In the control system industry, intrusion through external networks and USB memory sticks brought inside has attracted attention in recent years. On the other hand, for some reason, intrusions through LAN cables and optical cables, which are major components of networks, seem to receive less attention. Regardless of the control system, cyber-attacks are mostly conducted via the internet, so intrusion through LAN cables and optical cables, which require physical intrusion, might not receive much attention. While there is a lot of talk about wireless LAN security, I feel that there is not enough discussion about LAN cables inside buildings or fiber optic cables in the city. Attackers exploit weaknesses that defenders overlook. We would like you to consider security measures after understanding that LAN cables and optical cables, which we feel receive little attention, are not necessarily safe.
Are LAN Cables Safe for Security?
Suppose a personal computer is connected to a switching hub with a LAN cable. If someone unplugs the LAN cable from the connector or physically disconnects the LAN cable and pinches the hub, they can access the network from there. A person with knowledge of networking might think, "If I lock the LAN cable so that it cannot be disconnected from the connector, it cannot be disconnected, and I can notice something wrong if I monitor the dead/alive status regularly. If we regularly monitor system health, we will be able to notice if something strange is happening. But is it possible to detect it?
In this paper, we first tested the possibility of intrusion and eavesdropping by cutting LAN cables and making LAN cables by ourselves, for those who do not know that it is possible to intrude through LAN cables. Next, we tested that it is possible to intrude and eavesdrop in a short time by using a device called "Gutto Su" plug.
Intrusion and Eavesdropping Experiments
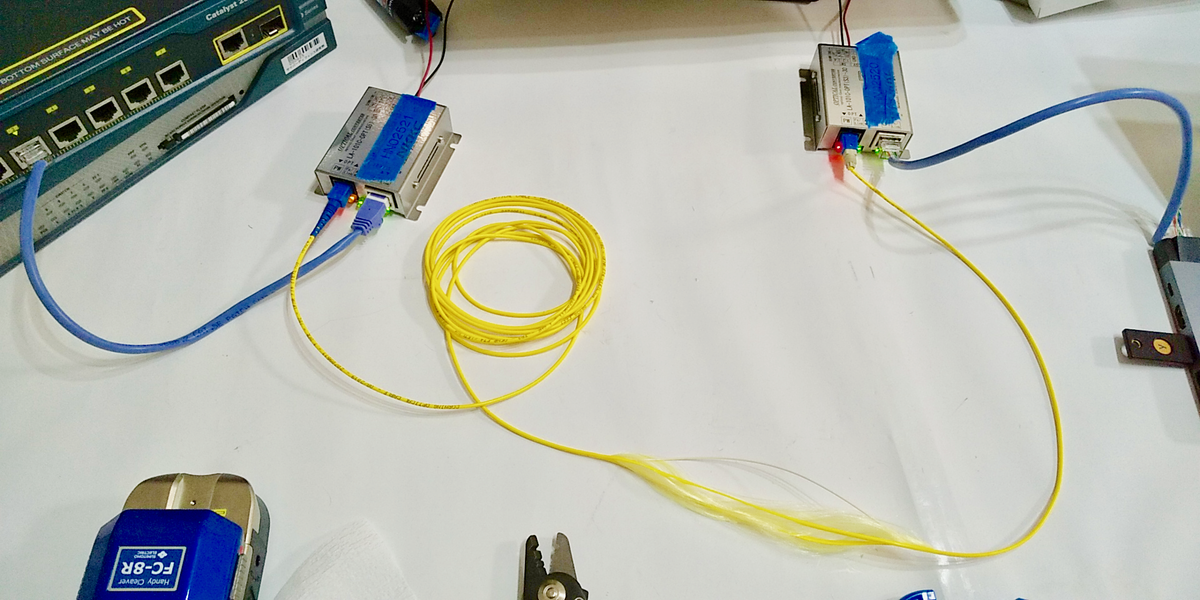
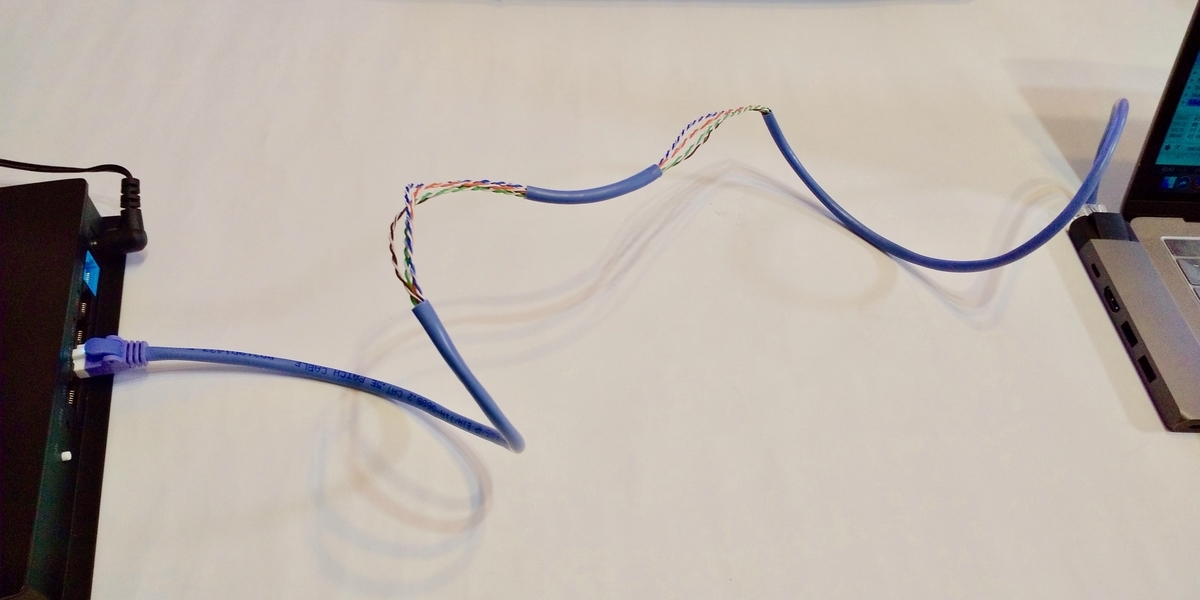
In the experiment, we connected a notebook PC (shown in Figure 1) to a switching hub with a LAN cable as the target of intrusion and eavesdropping. The notebook PC continuously sent ping packets to the switching hub, creating an environment for the experiment. Ping communication involves sending packets from the notebook PC in 1-second cycles, with the switching hub receiving the packets and returning response packets to the notebook PC.


Figure 1:Intrusion/eavesdropping target network
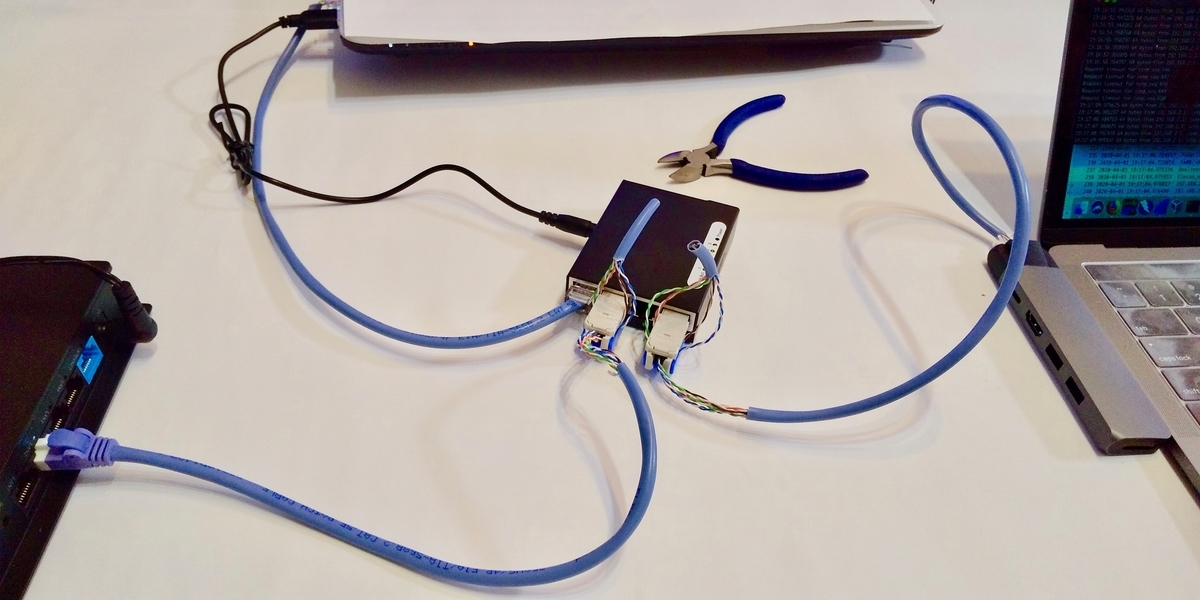
We prepared a repeater hub (shown in Figure 2) and a PC for eavesdropping.
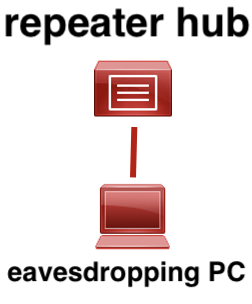

Figure 2:Repeater hub and PC for eavesdropping
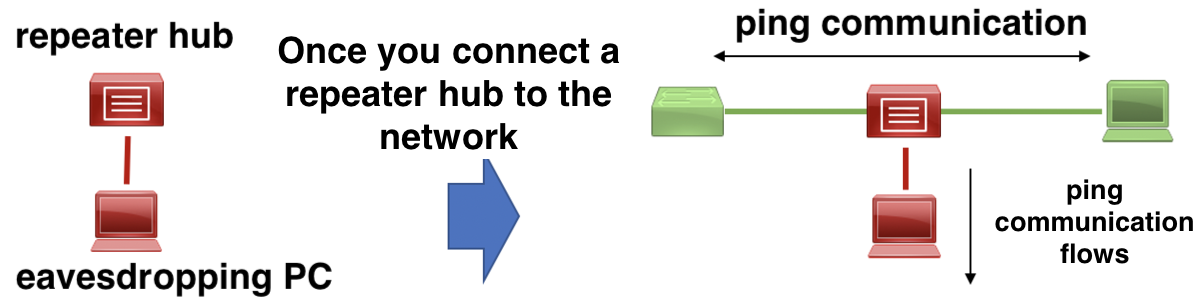
Figure 3: Image of packet capture using a repeater hub
Before the following experiments, we provide an overview of network intrusion and eavesdropping. For network intrusion, we cut the LAN cable between the notebook PC and the switching hub with nippers and placed a repeater hub between the cut LAN cables. This setup allowed communication packets flowing between the notebook PC and the switching hub to flow through the repeater hub to the eavesdropping PC, enabling Wireshark to eavesdrop. In this experiment, we measured the time it took for Wireshark to eavesdrop on ping communication after disconnecting the cable.
Experiment by Cutting LAN Cable and Making LAN Cable by Oneself
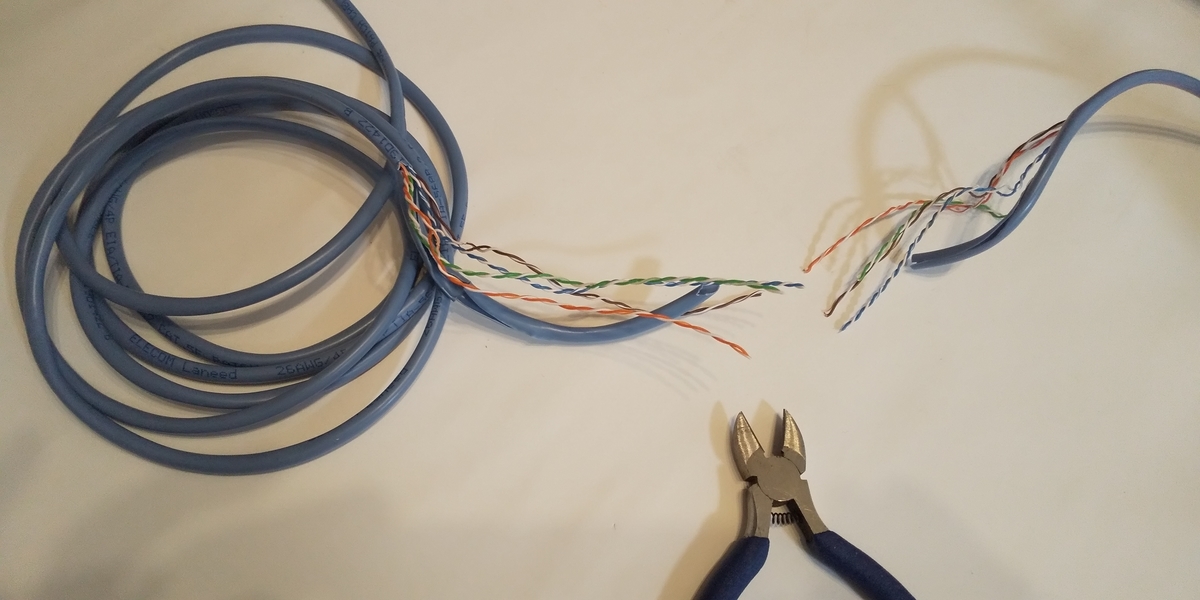
First, we tried cutting the LAN cable and making a LAN cable by ourselves.
Equipment used
| equipment | price |
|---|---|
| Sanwa Supply Crimping tool (with ratchet) LAN-TL8 | 3,482 yen |
| ELECOM RJ45 connector, single wire, 10 pieces, LD-RJ45T10A | 192yen |
| Nippers | Already owned |
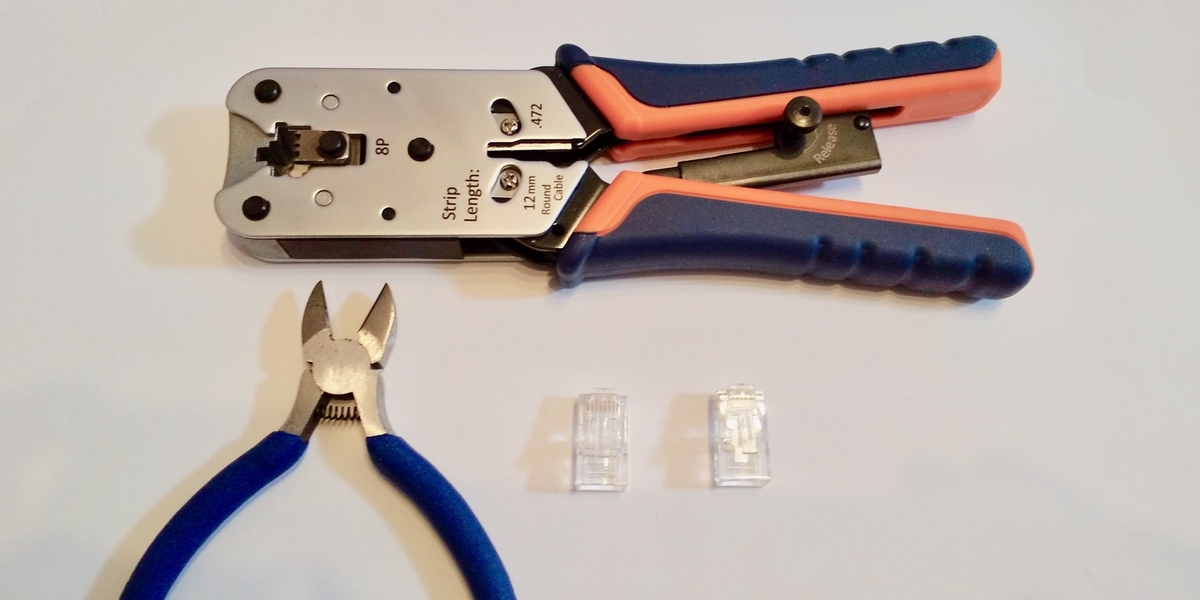
Cable making tools
Installation of repeater hub
- Cut the LAN cable between the notebook PC and the switching hub with nippers.
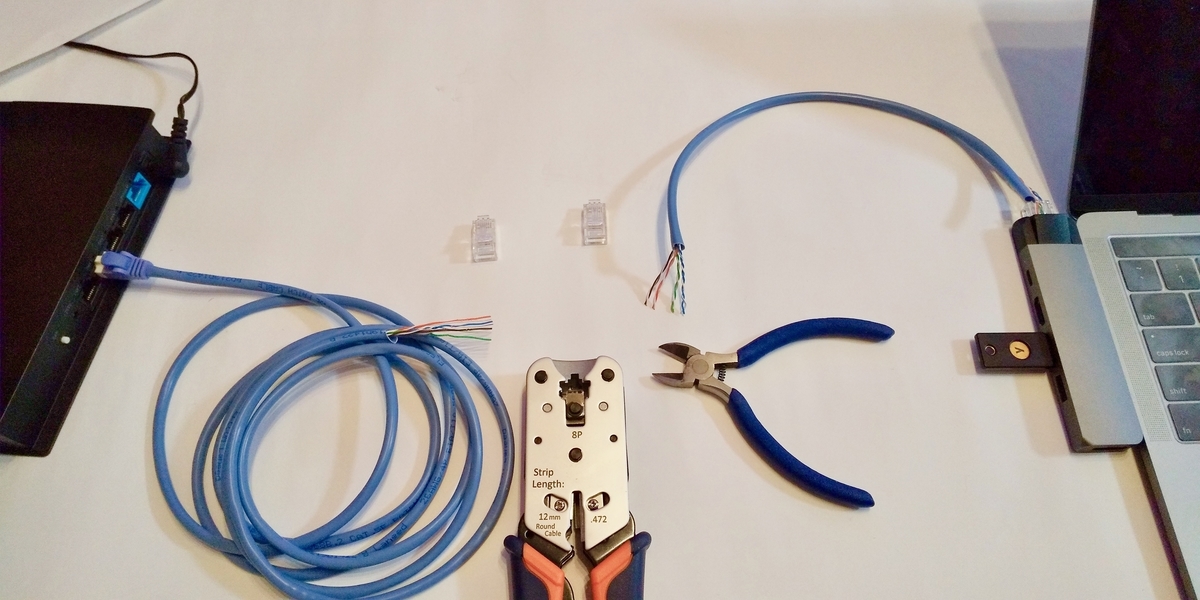
- Attach LAN connectors at the two cut points with a cable wrench tool.

- Connect the two LAN connectors to the repeater hub connected to the eavesdropping PC.

It took about 20 minutes to cut the cable with nippers and attach the LAN connectors, as I do not usually do this kind of work. Even for someone familiar with this kind of work, it might take a few minutes.
Measurement of Intrusion and Eavesdropping Time
After the above work, we confirmed that the Wireshark screen of the eavesdropping PC captured the ping packets of the notebook PC and the switching hub.
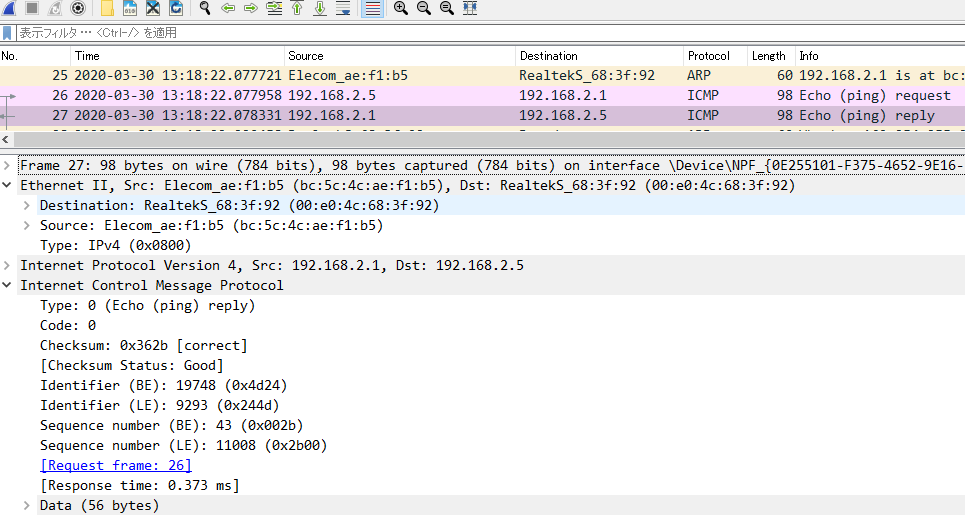
Since the communication was physically disconnected for over 20 minutes, you should be able to find it if, for example, you are monitoring for system health in one-minute cycles.
Experiment Using the Gutto Su plug Method
In the previous experiment, we found that disconnecting the LAN cable caused a communication breakdown every few minutes. This seemed to make it easy to detect communication breakdowns if we conducted health monitoring at regular intervals. However, we wanted to investigate if this was really the case.
In terms of work, all we had to do was disconnect the cable and insert a repeater hub in between. If we could work at high speed, the communication breakdown time would shorten. When searching for a suitable tool, we discovered the Gutto Su plug.
Note: The Gutto Su plug is a product designed for connecting LAN cables without special tools and is not intended for the kind of use introduced here
Equipment used
| Equipment | price |
|---|---|
| Panasonic Gutto Su plug CAT6 NR3555 x 2 | 1,238 yen |
| Cutter | Already owned |
| Nippers | Already owned |
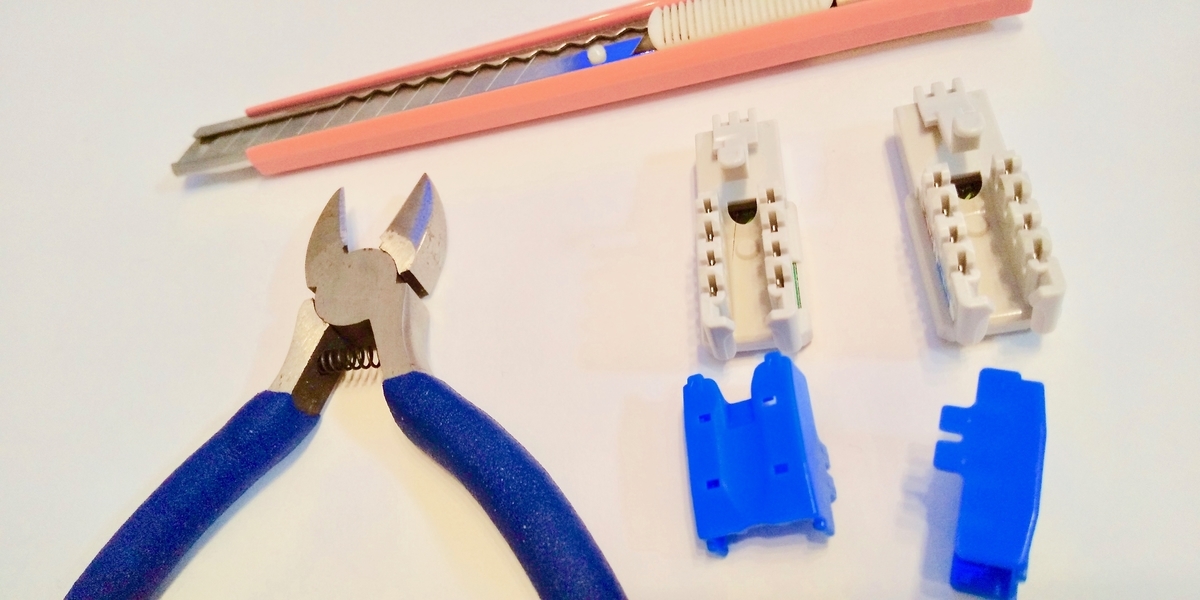
Gutto Su plug
Preparation before cutting LAN cable
-
Strip the sheath of the LAN cable with the cutter and pull out the stranded wires inside.
LAN cable with the sheath stripped off
-
Loosen the stranded wires and install the plug.
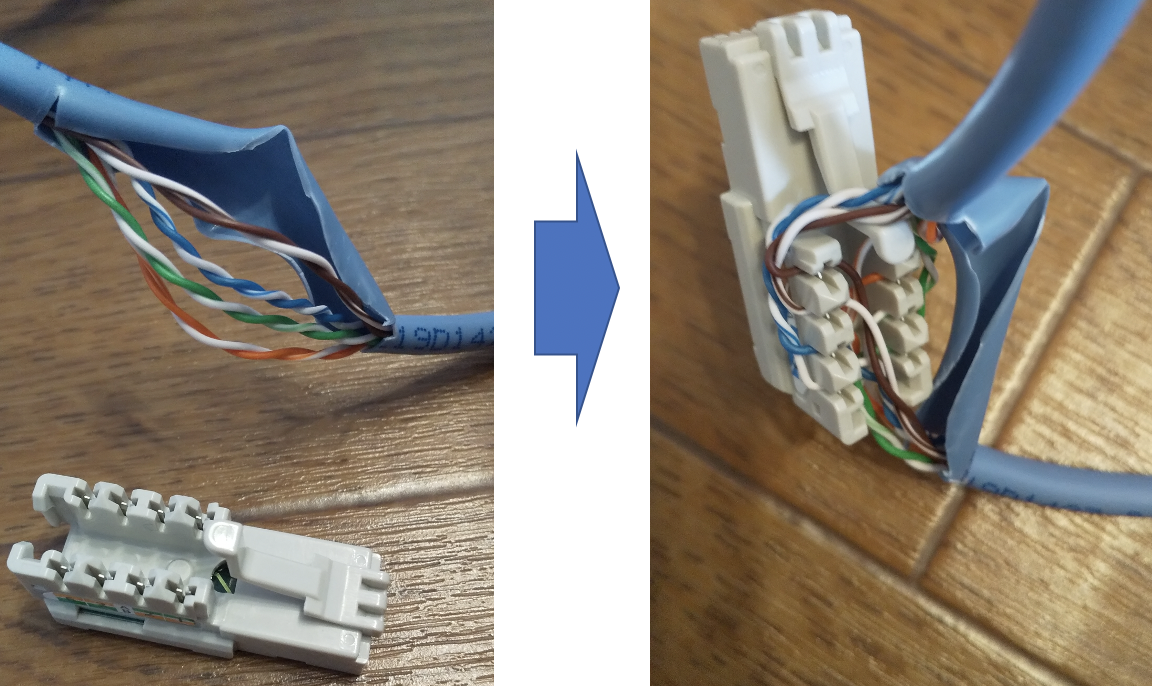
LAN cable is not snapped!

After installing the Gutto Su plug
At this point, the LAN cable is not snapped,so ping communication between the notebook PC and the switching hub remains uninterrupted.
Installation of repeater hub
-
The following image shows the preparation for connecting the two Gutto Su plugs to the repeater hub and cutting the LAN cable with nippers.
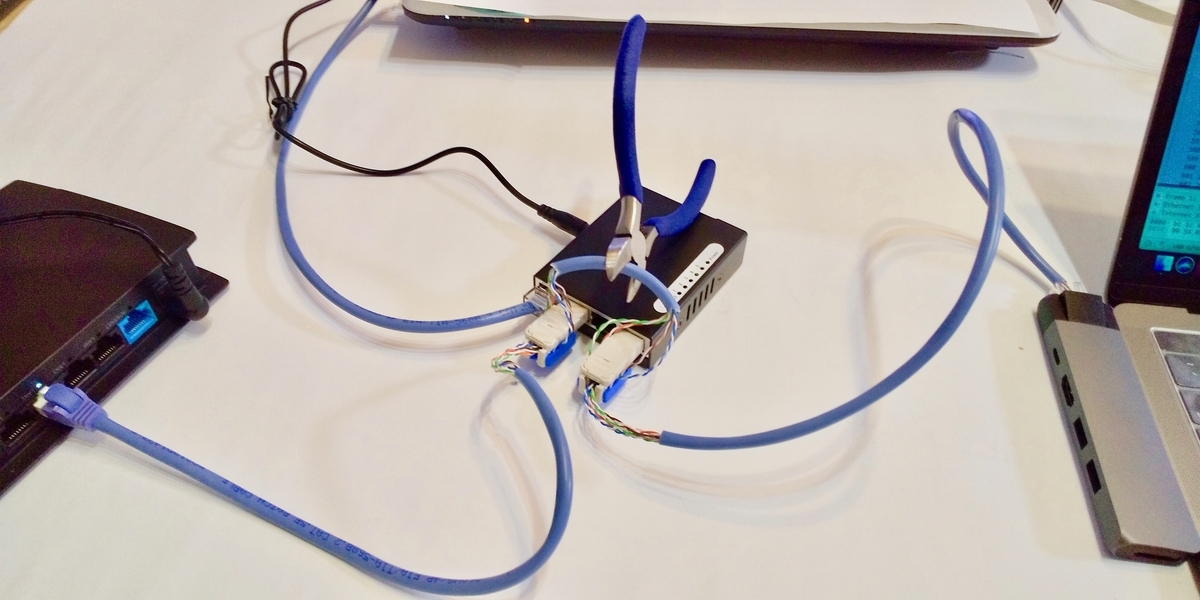
Just before cutting the LAN cable between the two plugs
-
The plug is not yet firmly attached to the connector of the repeater hub. Now, we cut the LAN cable with nippers and immediately insert the two Gutto Su plugs into the connector of the repeater hub.3, 2, 1, snap! click!
This figure shows two LAN connectors connected to the repeater hub.
Immediately after cutting the LAN cable between the Gutto Su plugs and connecting the connectors
It took 1 to 2 seconds to connect the Gutto Su plug to the connector of the repeater hub after cutting with nippers.
Measurement of intrusion time
It took 5 seconds after disconnection for the eavesdropping PC to capture packets of communication between the notebook PC and the switching hub.
For reference, here are the logs of the notebook PC and the Wireshark screen of the eavesdropping PC.
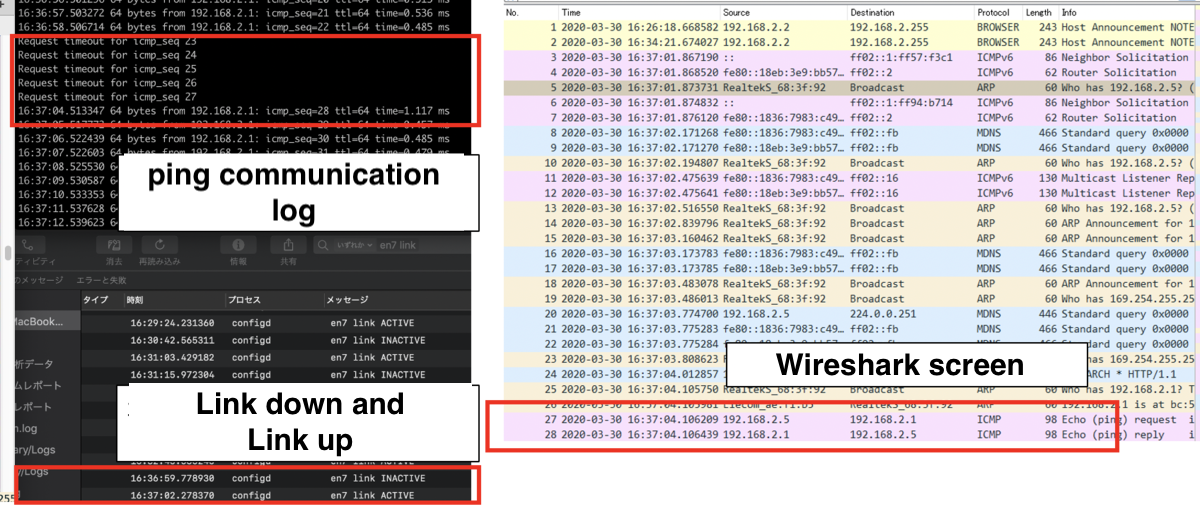
Time from cable disconnection to wiretap
Since the communication breakdown time was only 5 seconds, it might be difficult to detect a communication breakdown if, for example, you are monitoring for system health in one-minute cycles.
Physical Countermeasures and Monitoring Operation
In the event of a security incident, the methods described in this paper might help you identify an entry point. Being aware of various possibilities allows you to make more informed decisions when considering countermeasures.
In this experiment, we eavesdropped on ping communication. If important data is communicated in plain text, it could have been eavesdropped on using this technique. What countermeasures are effective against this technique? Encryption is the recommended countermeasure. However, in cases where encryption is not feasible due to budget constraints, locking LAN cables in the rooms where they are installed to prevent access might be effective. It could be challenging to install all LAN cables in locked rooms since they often connect under the floor or ceiling. Keeping suspicious people out of the building and conducting regular inspections to ensure that nothing unusual is physically connected to the LAN might also be good ideas. Detecting link breaks is another approach. Including LAN cable inspections in the scope of investigation during an incident might be an option as well. There is no single answer, so please consider what is realistic.
Note that while we disconnected the LAN cable in this experiment, it is also possible to eavesdrop without disconnecting it using different methods. As for the optical cable mentioned at the beginning of this article, penetrating it is not as easy as in this LAN cable experiment and requires time and skill. However, disconnecting the cable allows for penetration in terms of the mechanism. For more details, please refer to the article on fiber-optic wiretapping(japanese blog page).
Conclusion
We confirmed that cutting a LAN cable with nippers and penetrating and eavesdropping on a network within 5 seconds is possible. The purpose of this article is to inform you of the risk of cable tapping. We hope that this article helps you understand the threat of cable access and eavesdropping and that you can use this information in your security measures. We hope this article assists you in considering security measures.